Private, fast, always-on network
No single point of failure
Decentralized networks are inherently harder to attack, as they don’t contain substantial data silos, a preferred target for attackers. The lack of a single point of failure means that even if a single node is compromised, the network remains intact and operational.
Zero-knowledge architecture
Our network is designed around the concept of zero-knowledge, meaning that no sensitive information, confidential data, or private encryption keys are ever stored outside the communication devices. There is zero room for human error or internal data leakage.
Infinitely scalable
Each Encrypted Communication Node has a capacity for up to 3000 users. However, the technology allows for limitless and rapid scalability. New nodes can be easily deployed and added on demand.
Turnkey node deployment
New nodes can be deployed in a manner of minutes, thanks to the pre-configured turnkey installation.
Run your own private communication network

Join our global network and communicate with others
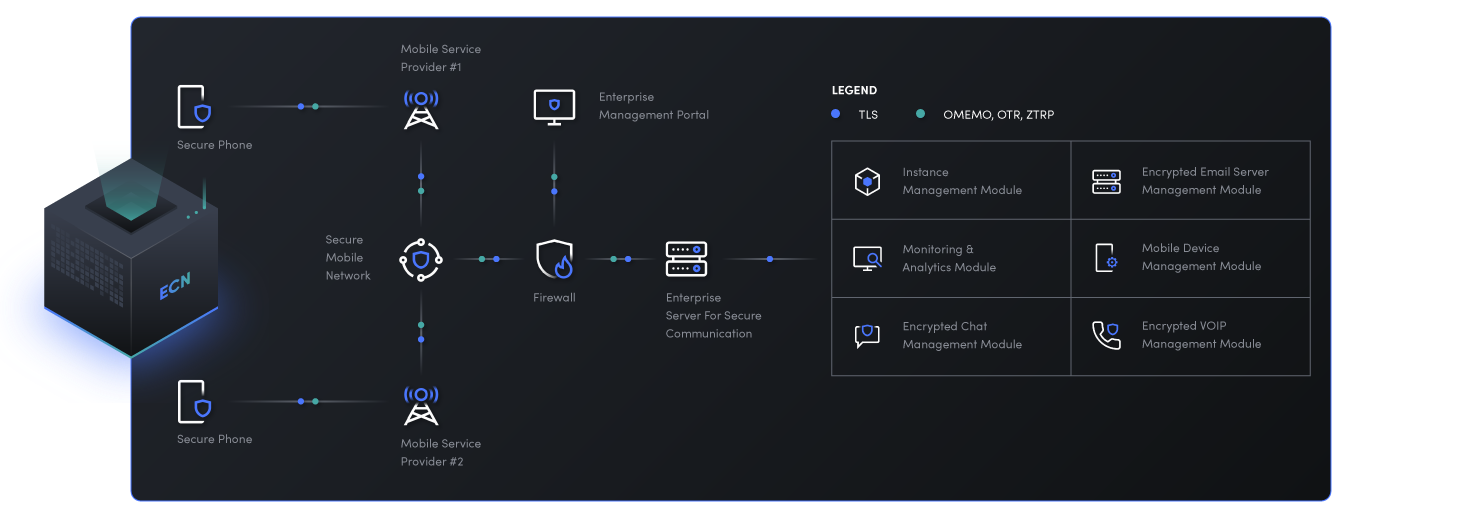
ECN Architecture
The advanced architecture of each Encrypted Communication Node (ECN) structures applications as a collection of microservices. This modular design allows for easy maintenance and expansion of functionalities if needed.
- Node capacity: 3000 users
- Scalability: new nodes can be added on-demand to increase capacity
Turnkey deployment
Spawn new nodes in a manner of minutes, thanks to the pre-configured turnkey installation. Or rely on one of our integration partners to do it for you.
Deployment options



On cloud

Dedicated organizations’ servers